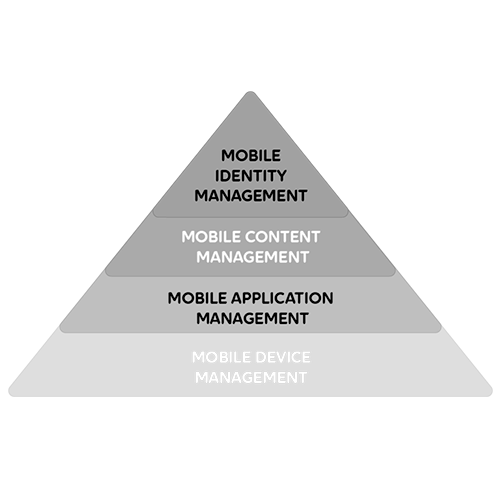
Unified Endpoint Management
When the number of devices within an organisation grows, it doesn’t have to mean that their management becomes more difficult. The solution is Unified Endpoint Management (UEM). UEM provides a single solution for managing all the company’s devices which are equipped with modern operating systems.
As well as devices, UEM allows the company to manage also its wireless network and email settings, for example. This ensures that its employees can focus on what’s important – the work itself.
Contact Us